Trust Wallet users affected by a recent browser extension hack are facing fresh delays after the wallet provider confirmed that its Chrome extension has been temporarily removed from the Chrome Web Store.
This resulted in slowing the rollout of a key claims verification tool tied to the incident.
Trust Wallet chief executive Eowyn Chen said the extension became unavailable after the company encountered a Chrome Web Store bug while attempting to release a new version.
The delayed update was meant to introduce a verification feature designed to help victims of the Christmas Day hack confirm wallet ownership and submit reimbursement claims securely.
Chen said Google has acknowledged the issue and is escalating it internally, while warning users to stay alert for fake or impersonated versions of the extension circulating online.
Attackers Exploited Fake Trust Wallet Update to Steal Funds
The outage comes as Trust Wallet continues to manage the fallout from a security breach that began unfolding in late December.
On December 25, the company confirmed that a malicious version of its Chrome browser extension, version 2.68, had been distributed through the Chrome Web Store outside its normal release process.
The compromised extension allowed attackers to access sensitive wallet data and execute unauthorized transactions, leading to millions of dollars in losses.
Trust Wallet’s internal investigation shows that only users who installed version 2.68 and logged into their wallets between December 24 and December 26 were affected.
Mobile app users, users on other extension versions, and those who installed or logged in after December 26 were not impacted.
The company said it identified 2,520 wallet addresses that were drained during the incident, with roughly $8.5 million in assets linked to 17 attacker-controlled wallets.
The wallet, though, noted that some of those attacker addresses also targeted wallets unrelated to Trust Wallet.
Security researchers later confirmed that the malicious build appeared legitimate and passed Chrome’s review process but contained hidden code capable of extracting recovery phrases.
Several users said simply importing a seed phrase into the extension triggered immediate fund outflows across multiple blockchains.
Trust Wallet Cleans Up Extension Hack; Flags Rise in Fake Compensation Scams
Trust Wallet traced the breach back to a wider supply chain attack known as Sha1-Hulud, which surfaced in November and affected multiple companies through compromised developer tooling.
The company said exposed GitHub secrets and a leaked Chrome Web Store API key allowed the attacker to upload the malicious extension directly, bypassing internal approval checks.
In response, Trust Wallet rolled back to a clean release, published version 2.69, and disabled compromised publishing credentials. It also declared a voluntary reimbursement scheme, which they promised to all those people who were found to be victims.
On December 29, it opened a formal claims process, where users are asked to provide wallet addresses, transaction hashes, and identifying information via an official support portal.
In its response to over 5,000 claims, the company indicated that it has been inundated with claims, given that the number of verified affected wallets is much lower, and it is a cause of concern that there could be duplicate or fake claims.
It is the cause of that discrepancy that led to the creation of another verification mechanism that was supposed to be provided with the next update of the browser extension, but was delayed by the Chrome Web Store problem.
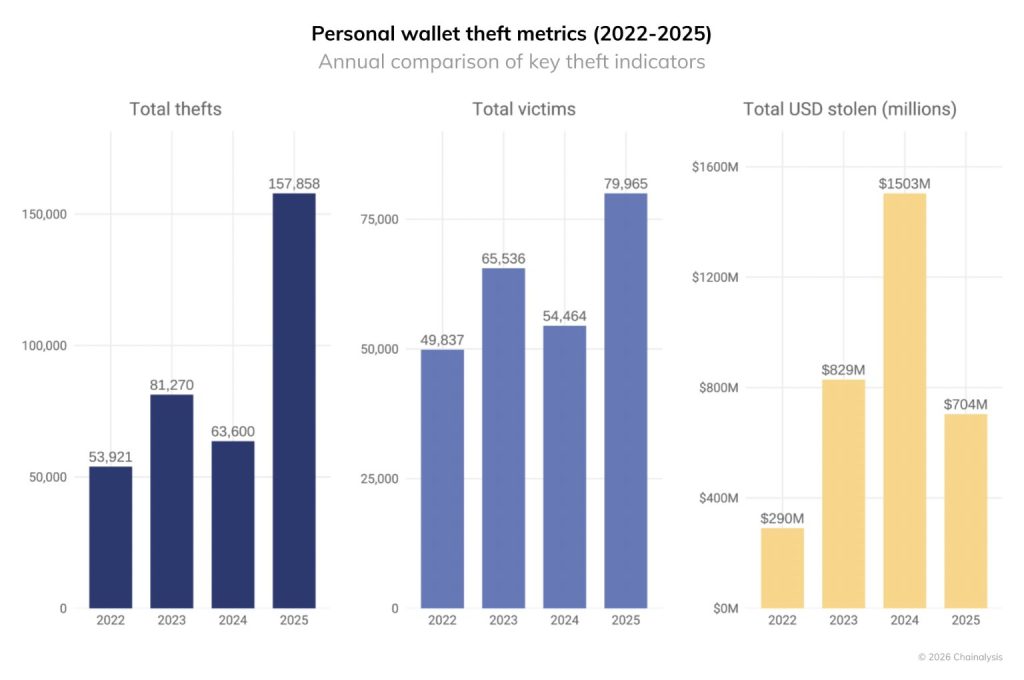
The event continues to add to an increasing number of wallet-related escapades in the crypto industry.
Industry data shows that the proportion of personal wallet compromises has continued to increase as the share of stolen funds.
https://cryptonews.com/news/trust-wallet-chrome-bug-delays-hack-reimbursement/