A security breach tied to decentralized exchange aggregator Matcha Meta has resulted in the theft of roughly $16.8 million in crypto assets, adding to a growing list of smart-contract exploits that continue to test the safety assumptions of DeFi users.
The incident unfolded on Sunday and was traced not to Matcha’s core infrastructure, but to SwapNet, one of the liquidity providers integrated into the platform.
Matcha Meta disclosed the issue publicly in a post on X, saying users who had disabled its “One-Time Approval” feature and instead granted direct token allowances to individual aggregator contracts may have been exposed.
The protocol urged affected users to immediately revoke approvals connected to SwapNet’s router contract, warning that failure to do so could leave wallets vulnerable to further unauthorized transfers.
$17M Vanishes in Seconds: How Matcha Hackers Slipped Funds Onto Ethereum
Blockchain security firms quickly began tracking the exploit as funds moved on-chain.
PeckShield reported that approximately $16.8 million had been drained in total, with the attacker swapping around $10.5 million in USDC for roughly 3,655 ETH on the Base network before starting to bridge assets to Ethereum.
CertiK independently flagged suspicious transactions, identifying one wallet that siphoned about $13.3 million in USDC on Base and converted the funds into wrapped Ether.
Both firms pointed to a vulnerability in the SwapNet contract that allowed arbitrary calls, enabling the attacker to transfer tokens that users had previously approved.
Matcha later clarified that the incident was not connected to 0x’s AllowanceHolder or Settler contracts, which underpin its One-Time Approval system.
The team noted that users who interacted with Matcha using One-Time Approvals were not affected, as this design limits how much access a third-party contract can retain.
The exposure, the team said, applied only to users who opted out of that system and granted ongoing allowances directly to aggregator contracts. In response, Matcha has removed the option for users to set such direct approvals going forward.
Old Token Approvals Emerge as a Persistent DeFi Weak Spot
The breach highlights a recurring tension in DeFi between flexibility and safety. Token approvals, while necessary for interacting with smart contracts, have long been a weak point, particularly when permissions remain active long after a transaction is completed.
In this case, previously granted allowances became the pathway for the exploit once the SwapNet contract was compromised.
The incident arrives amid continued concerns over smart-contract security across the crypto sector.
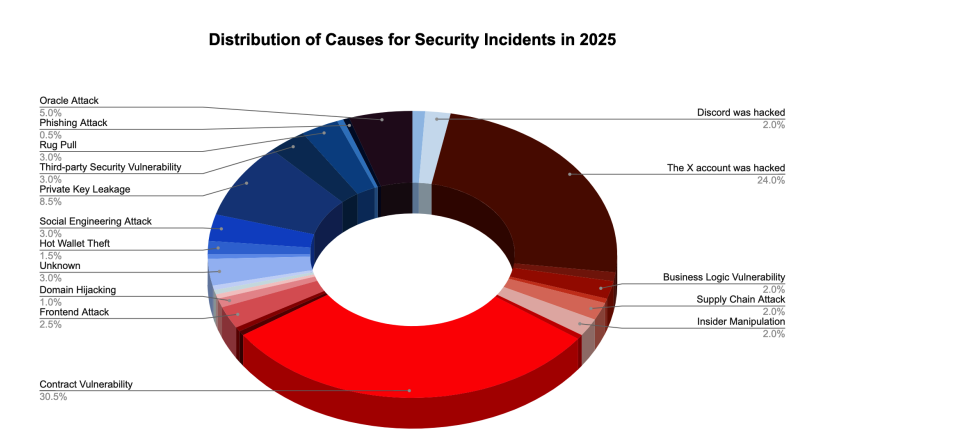
SlowMist’s year-end report shows that vulnerabilities in smart contracts accounted for just over 30% of crypto exploits in 2025, making them the leading cause of losses.
Researchers have also warned that advances in artificial intelligence are accelerating how quickly attackers can identify and exploit weaknesses in on-chain code.
While overall crypto losses declined in December, falling about 60% month-on-month to roughly $76 million, security firms cautioned that the drop did not reflect a structural improvement.
PeckShield noted that a single address-poisoning scam accounted for $50 million of December’s losses, showing how concentrated and severe individual incidents can be even during quieter periods.
January has already seen several notable exploits. IPOR Labs confirmed a $336,000 attack on its USDC Fusion Optimizer vault on Arbitrum, while Truebit disclosed a smart-contract incident that on-chain analysts estimate drained more than 8,500 ETH, triggering a near-total collapse in the project’s token price.
Last week, Layer-1 network Saga paused its SagaEVM chain after an exploit moved close to $7 million in assets to Ethereum.
https://cryptonews.com/news/matcha-meta-16-8m-swapnet-exploit-users-warned/