A newly discovered malicious Chrome extension is stealing funds from Solana traders by quietly siphoning a fee from every swap they execute, according to new findings from Socket’s Threat Research Team.
The extension, called Crypto Copilot, has been available on the Chrome Web Store since June 2024 and markets itself as a shortcut for executing Solana trades directly from users’ X feeds.
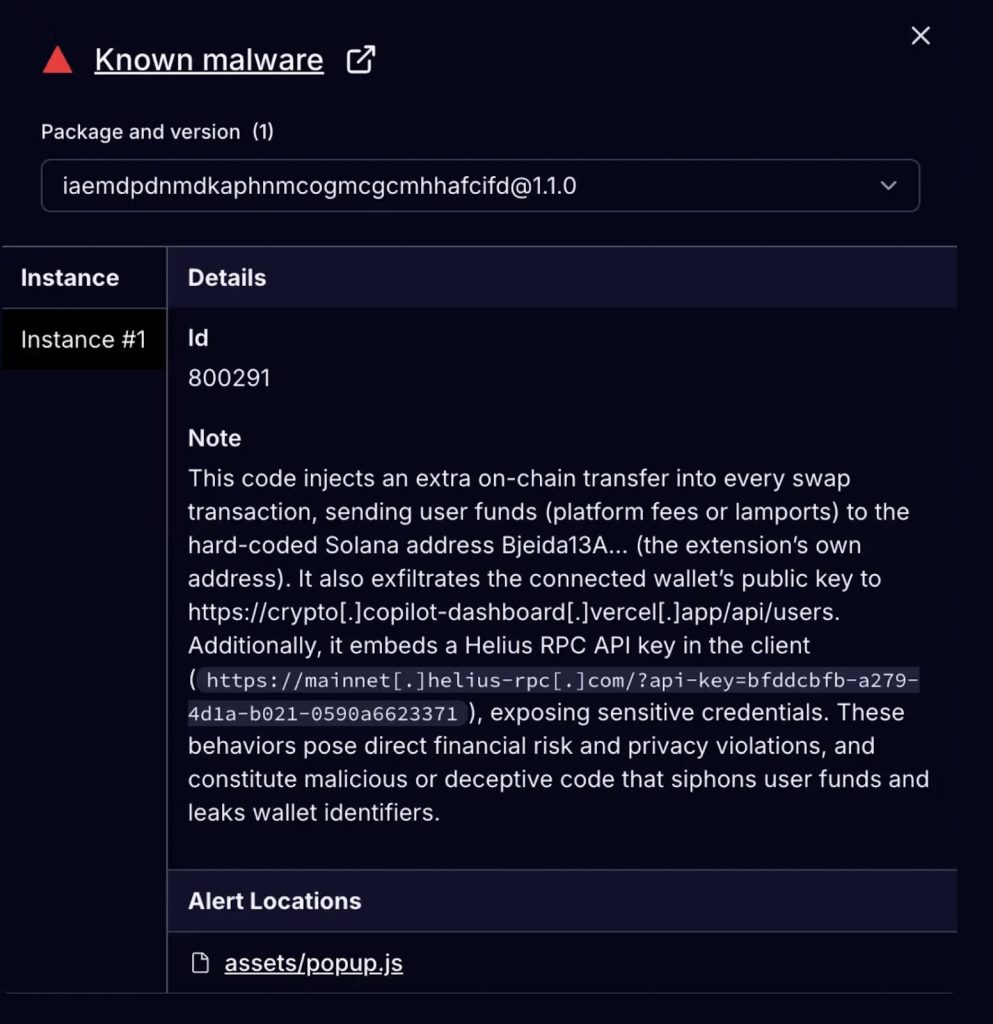
Behind the interface, however, researchers found code designed to insert an additional transfer into each Raydium swap, diverting at least 0.0013 SOL, or 0.05% of each transaction, to an attacker-controlled wallet.
Crypto Copilot Sends Wallet Data to Suspicious Backend While Draining Trader Funds
Socket researchers say the extension constructs a normal Raydium swap instruction but then appends a second instruction that transfers SOL to the wallet address Bjeida.
Users only see the legitimate swap in the interface, and most wallet confirmation windows display only a high-level summary of the transaction rather than the full list of instructions.
As a result, traders approve what appears to be a standard transaction, unaware of the hidden transfer embedded inside it.
The fee logic is fully hardcoded inside the extension and buried under layers of obfuscated JavaScript.
Socket notes that the extension applies whichever is greater between the minimum fee and the percentage-based fee, meaning trades above 2.6 SOL incur the full 0.05% extraction.
Researchers found that the extension uses variable renaming and aggressive minification to conceal the behavior, and the attacker’s wallet is labeled under an innocuous variable deep inside the bundle.
The extension remains online at the time of reporting. Socket says it has submitted a takedown request to Google, but has not received confirmation that action has been taken.
Beyond the fee theft, investigators also discovered that Crypto Copilot connects to a backend hosted on crypto-coplilot-dashboard.vercel.app, a misspelled domain that shows only a blank placeholder page.
Despite the empty site, the extension regularly sends connected wallet identifiers and activity data to this backend, along with using a hardcoded Helius API key for transaction simulation and RPC calls.
A separate domain tied to the tool, cryptocopilot.app, is currently parked.
Researchers say the absence of documentation, a functioning dashboard, or any supporting infrastructure is inconsistent with a legitimate trading product and instead reflects common practices seen in malicious browser extensions.
While on-chain activity linked to the attacker’s wallet remains limited, investigators believe the low transaction volume likely reflects the extension’s relatively small distribution rather than an absence of risk.
They warn that the mechanism scales with trading activity, meaning high-volume users could lose larger amounts over time without noticing the incremental drain.
Crypto Losses Fall to 2025 Lows, but Browser Extension Attacks Continue to Climb
The discovery comes during a period of heightened scrutiny around browser-based crypto threats. In July, more than 40 malicious Firefox extensions were found impersonating major wallet providers, including MetaMask, Coinbase, Phantom, OKX, and Trust Wallet.
Those extensions harvested wallet credentials directly from users’ browsers and transmitted them to attacker-controlled servers.
Exchanges such as OKX publicly warned users and filed complaints after discovering fake plugins masquerading as official wallet tools. Browser extensions have emerged as one of the most persistent attack vectors in 2025, contributing to a growing share of crypto losses.
Wallet-related breaches accounted for $1.7 billion of the $2.2 billion stolen across the first half of the year, according to CertiK. Phishing incidents added another $410 million.
Despite the rise in extension-based threats, the broader crypto sector briefly experienced a decline in successful hacks.
PeckShield recorded just $18.18 million stolen across 15 incidents in October, the lowest monthly total of the year.
That figure had been far higher a month earlier when losses reached $127.06 million in September, driven by nearly 20 major exploits. But even as overall losses dipped, high-profile breaches continued.
https://cryptonews.com/news/crypto-copilot-solana-extension-hidden-fee/